Report the ad
Ccna7 in fsd career institute - Faisalabad
Sunday, 22 December 2019Item details
City:
Faisalabad, Punjab
Offer type:
Offer
Price:
Rs 25,000
Item description
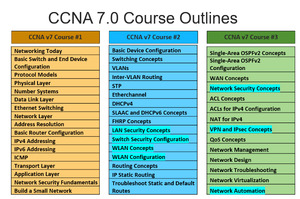
New Module: LAN Security Concepts
•Endpoint Security: Network attacks, Security devices, Endpoint Protection, Email and Web Security
•Access Control: Local Password, Authentication, Authorization, Accounting, 802.1x
•Security Threats: Layer 2 Vulnerabilities, Switch Attack Categories, Switch attack mitigation techniques
•MAC Address Table Attacks and mitigation
•LAN Attacks: VLAN Hopping, VLAN Double Tagging, DHCP Attacks, ARP Attacks, Address Spoofing attacks, STP Attacks, CDP Reconnaissance
New Module: Switch Security Configuration
•Implement Port Security: Secure unused ports, Mitigate MAC Address Table Attacks, Enable Port Security, Limit and Learn MAC Addresses, Port Security Aging, Port Security Violation Modes, Ports in err-disabled state, Verify Port Security
•Mitigate VLAN Attacks: Mitigate VLAN Hopping
•Mitigate DHCP Attacks: DHCP Snooping, Configuration
•Mitigate ARP Attacks: Dyn ARP Inspection, DAI Implementation
•Mitigate STP Attacks: PortFast and BPDU Guard, Configuration
New Module: WLAN Concepts
•Introduction to Wireless: Benefits of Wireless, Type of Wireless networks, Wireless Technologies, 802.11, Radio Frequencies, Wireless Standards Organizaions
•WLAN Components: Wireless NIC, Wireless Home Router, Wireless Access Point, AP Categories, Wireless Antennas
•WLAN Operation: 802.11 Modes, BSS and ESS, 802.11 Frame Structure, CSMA/CA, Client and AP Association, Passive and Active discovery
•CAPWAP Operation: Introduction to CAPWAP, Split MAC Architecture, DTLS Encryption, FlexConnect APs
•Channel Management: Frequency Channel Saturation, Channel Selection, Planning a WLAN Deployment
•WLAN Threats: DoS attacks, Rouge Access Points, MITM Attack
•Secure WLANs: SSID Cloaking and MAC Filtering, 802.11 Original Auth. Methods, Shared Key auth. Methods, Authenticating a home user, Encryption Methods, Auth. In the Enterprise, WPA3
New Module: WLAN Configuration
•Remote Site WLAN Configuration: Wireless Router, Log in to Wireless Router, Basic Network setup, Configure a wireless mesh network, NAT for IPv4, QoS
•Configure a Basic WLAN on the WLC: WLC Topology, Log into the WLC, View AP Information, Advanced Settings, Configure a WLAN
•Configure a WPA2 Enterprise WLAN on the WLC: SNMP and RADIUS, Configure SNMP Server Information, Configure RADIUS Server Information, Configure a VLAN for a New WLAN, Topology with VLAN 5 Addressing, Configure a new Interface, Configure a DHCP in a new WLAN, Configure DHCP Scope, Configure WPA2 Enterprise WLAN
•Troubleshoot WLAN Issues: Wireless Client not connecting, Network is slow, Updating Firmware
New Module: Network Security Concepts
•Current State of Cybersecurity: Current state of Affairs, Vectors of network attacks, Data Loss
•Threat Actors: The Hacker, Evolution of Hackers, Cyber Criminals, Hacktivists, State-Sponsored Hackers
•Threat Actor Tools: Attack Tools, Evolution of Security Tools, Attack Types
•Malware: Viruses and Trojan Horses, Types of Malware
•Common Network Attacks: Reconnaissance, Access, Social Engineering, Dos and DDoS
•IP Vulnerabilities and Threats: ICMP, Amplification and Reflection, Address Spoofing Attacks
•TCP and UDP Vulnerabilities: TCP and UDP Segment Header, TCP Services, TCP Attacks, UDP Attacks
•IP Services: ARP Vulnerabilities, ARP Cache poisoning, DNS Attacks, DNS Tunneling, DHCP Attacks
•Network Security Best Practices: CIA, Defence-in-Depth approach, Firewalls, IPS, Content Security Appliances
•Cryptography: Securing communication, Data Integrity, Hash Functions, Origin Auth., Data Confidentiality, Symmetric Encryption, Asymmetric Encryption, Deffie-Helman
New Module: VPN and IPsec Concepts
•VPN Technology: VPN Benefits, Site-to-Site and Remote-access VPN, Enterprise and Service provider VPN
•Types of VPN: Remote-access, SSL, Site-to-Site IPsec, GRE over IPsec, DMVPN, IPsec Virtual Tunnel Interface, Service Provider MPLS
•IPsec: IPsec concepts, IPsec technologies, IPsec protocol encapsulation, Confidentiality, Integrity, Authentication, Secure Key Exchange with DH, IPsec transport and Tunnel modes
New Module: Network Automation
•Automation Overview
•Data Formats: Data formats concept, data format rules, JSON, YAML, XML
•APIs: API Concept, API Example, Open, Internal and Partner APIs, Types of Web Service APIs
•REST: REST and RESTful API, RESTful implementation, URI/URN/URL, Anatomy of RESTful Request, RESTful API Applications
•Configuration Management Tools: Traditional Network Configuration, Network Automation, Ansible, Chef, Puppet, SaltStack
•IBN and Cisco DNA Center: Intent Based Networking, Network Infrastructure as Fabric, Cisco DNA, CDA Center
•Endpoint Security: Network attacks, Security devices, Endpoint Protection, Email and Web Security
•Access Control: Local Password, Authentication, Authorization, Accounting, 802.1x
•Security Threats: Layer 2 Vulnerabilities, Switch Attack Categories, Switch attack mitigation techniques
•MAC Address Table Attacks and mitigation
•LAN Attacks: VLAN Hopping, VLAN Double Tagging, DHCP Attacks, ARP Attacks, Address Spoofing attacks, STP Attacks, CDP Reconnaissance
New Module: Switch Security Configuration
•Implement Port Security: Secure unused ports, Mitigate MAC Address Table Attacks, Enable Port Security, Limit and Learn MAC Addresses, Port Security Aging, Port Security Violation Modes, Ports in err-disabled state, Verify Port Security
•Mitigate VLAN Attacks: Mitigate VLAN Hopping
•Mitigate DHCP Attacks: DHCP Snooping, Configuration
•Mitigate ARP Attacks: Dyn ARP Inspection, DAI Implementation
•Mitigate STP Attacks: PortFast and BPDU Guard, Configuration
New Module: WLAN Concepts
•Introduction to Wireless: Benefits of Wireless, Type of Wireless networks, Wireless Technologies, 802.11, Radio Frequencies, Wireless Standards Organizaions
•WLAN Components: Wireless NIC, Wireless Home Router, Wireless Access Point, AP Categories, Wireless Antennas
•WLAN Operation: 802.11 Modes, BSS and ESS, 802.11 Frame Structure, CSMA/CA, Client and AP Association, Passive and Active discovery
•CAPWAP Operation: Introduction to CAPWAP, Split MAC Architecture, DTLS Encryption, FlexConnect APs
•Channel Management: Frequency Channel Saturation, Channel Selection, Planning a WLAN Deployment
•WLAN Threats: DoS attacks, Rouge Access Points, MITM Attack
•Secure WLANs: SSID Cloaking and MAC Filtering, 802.11 Original Auth. Methods, Shared Key auth. Methods, Authenticating a home user, Encryption Methods, Auth. In the Enterprise, WPA3
New Module: WLAN Configuration
•Remote Site WLAN Configuration: Wireless Router, Log in to Wireless Router, Basic Network setup, Configure a wireless mesh network, NAT for IPv4, QoS
•Configure a Basic WLAN on the WLC: WLC Topology, Log into the WLC, View AP Information, Advanced Settings, Configure a WLAN
•Configure a WPA2 Enterprise WLAN on the WLC: SNMP and RADIUS, Configure SNMP Server Information, Configure RADIUS Server Information, Configure a VLAN for a New WLAN, Topology with VLAN 5 Addressing, Configure a new Interface, Configure a DHCP in a new WLAN, Configure DHCP Scope, Configure WPA2 Enterprise WLAN
•Troubleshoot WLAN Issues: Wireless Client not connecting, Network is slow, Updating Firmware
New Module: Network Security Concepts
•Current State of Cybersecurity: Current state of Affairs, Vectors of network attacks, Data Loss
•Threat Actors: The Hacker, Evolution of Hackers, Cyber Criminals, Hacktivists, State-Sponsored Hackers
•Threat Actor Tools: Attack Tools, Evolution of Security Tools, Attack Types
•Malware: Viruses and Trojan Horses, Types of Malware
•Common Network Attacks: Reconnaissance, Access, Social Engineering, Dos and DDoS
•IP Vulnerabilities and Threats: ICMP, Amplification and Reflection, Address Spoofing Attacks
•TCP and UDP Vulnerabilities: TCP and UDP Segment Header, TCP Services, TCP Attacks, UDP Attacks
•IP Services: ARP Vulnerabilities, ARP Cache poisoning, DNS Attacks, DNS Tunneling, DHCP Attacks
•Network Security Best Practices: CIA, Defence-in-Depth approach, Firewalls, IPS, Content Security Appliances
•Cryptography: Securing communication, Data Integrity, Hash Functions, Origin Auth., Data Confidentiality, Symmetric Encryption, Asymmetric Encryption, Deffie-Helman
New Module: VPN and IPsec Concepts
•VPN Technology: VPN Benefits, Site-to-Site and Remote-access VPN, Enterprise and Service provider VPN
•Types of VPN: Remote-access, SSL, Site-to-Site IPsec, GRE over IPsec, DMVPN, IPsec Virtual Tunnel Interface, Service Provider MPLS
•IPsec: IPsec concepts, IPsec technologies, IPsec protocol encapsulation, Confidentiality, Integrity, Authentication, Secure Key Exchange with DH, IPsec transport and Tunnel modes
New Module: Network Automation
•Automation Overview
•Data Formats: Data formats concept, data format rules, JSON, YAML, XML
•APIs: API Concept, API Example, Open, Internal and Partner APIs, Types of Web Service APIs
•REST: REST and RESTful API, RESTful implementation, URI/URN/URL, Anatomy of RESTful Request, RESTful API Applications
•Configuration Management Tools: Traditional Network Configuration, Network Automation, Ansible, Chef, Puppet, SaltStack
•IBN and Cisco DNA Center: Intent Based Networking, Network Infrastructure as Fabric, Cisco DNA, CDA Center